- Blog
- Fraud For Sale: Multi-accounting and Fraud on Gig Economy Apps
Fraud For Sale: Multi-accounting and Fraud on Gig Economy Apps
Fraud-as-a-Service isn’t a new phenomenon, but it is a growing one. Using FaaS tools, fraudsters can create fake accounts, bypass biometric facial verification, scale their operations, commit ban evasion, and more.
Subscribe to the Incognia Newsletter
For those who prefer listening over reading, we've provided an audio transcription player below, allowing you to enjoy this post through your speakers or headphones.
Fraud-as-a-service is a business model wherein one fraudster sells tools, tactics, or services to another in order to make fraud easier or more profitable.
Fraud-as-a-Service has targets across industries, but with the explosion of the gig economy in the past decade, gig economy platforms have drawn the attention of career fraudsters. Using tools like the ones mentioned below, fraudsters can scale their operations and make a living at a platform’s expense.
Key TakeAways
- Some fraudsters make tools for other fraudsters to make fraud easier, faster, and more cost efficient—these tools are called Fraud-as-a-Service or FaaS tools
- FaaS tools can make multi-accounting easier to commit and scale, improving fraudster ROI
- Fraudsters and other bad actors use these FaaS tools to target gig economy apps with schemes like promo abuse
Multi-accounting and fraud on gig economy apps
“If you have fake accounts, you can do pretty much any type of scam.”
This is what Incognia’s Global Head of Industry, Eduardo Pires, had to say about multi-accounting during the About Fraud webinar, “Unmasking the Advanced Tools Powering Fraud-as-a-Service.”
And it’s true. Having multiple accounts to rely on is the backbone of any organized mobile fraud operation. There are two main reasons for this.
With multiple accounts you can:
- Avoid accountability by using extra accounts to commit ban evasion
- Scale your operation to make as much money as possible
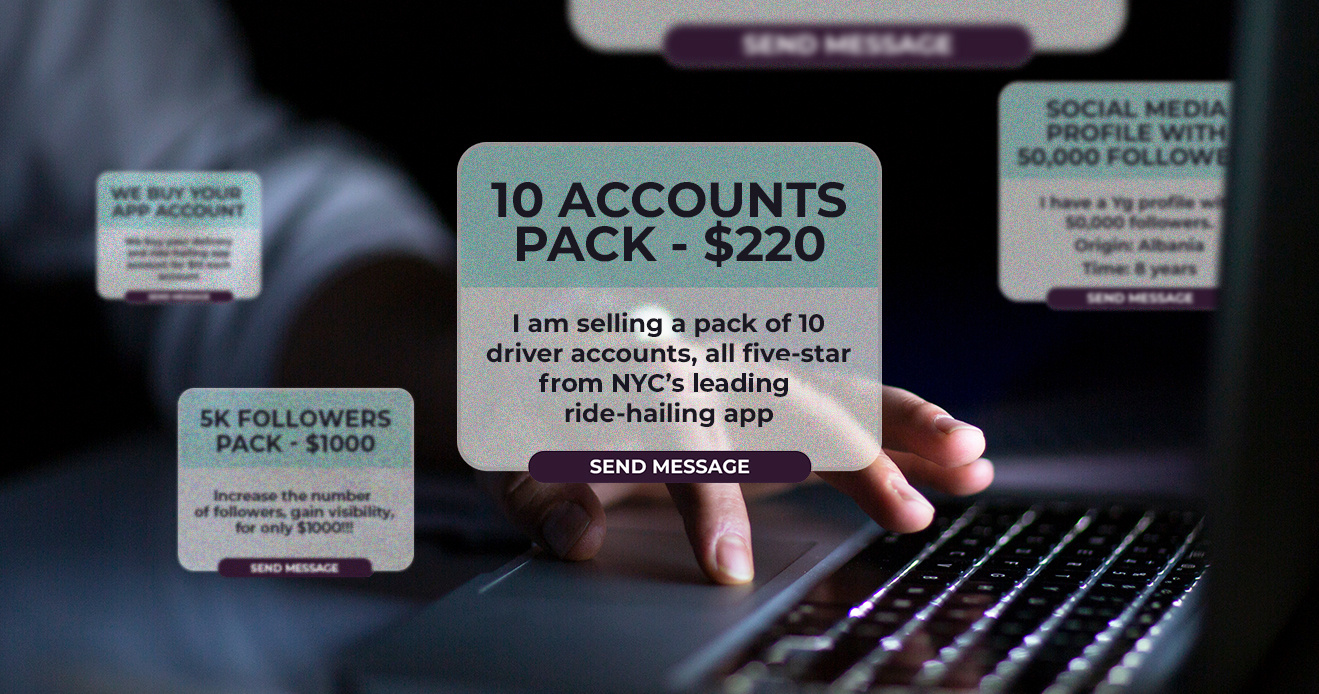
Because of the importance of multiple accounts to committing organized fraud attacks on gig platforms, many Fraud-as-a-Service tools that target gig apps revolve around making it easier, faster, and more efficient to create multiple accounts.
Sometimes, multiple accounts are a FaaS product themselves—in group chats or on forums, bad actors might sell “packs” of pre-created accounts, or identity-verified accounts one at a time.
Emulators and app cloners
Having the extra fake accounts to lean on is only one part of the equation. You also need an easy way to switch between accounts, or else you’re wasting too much time (like anyone else, fraudsters are thinking about how much their time is worth).
Logging in and out of each account manually when you’re managing hundreds of accounts gets tedious fast. To help maximize their account management and reach, fraudsters have a powerful combination up their sleeves: app cloners and emulators.
Here’s a quick emulator explanation from Eduardo:
“Emulators were basically created to help software developers test software. So, imagine that you are a programmer from Uber. Uber is operating in multiple regions across the globe with thousands of different device models. So we have to test the software in different configurations.
“And so an emulator is a way of creating a virtual device in your desktop computer. It was originally used to test software. But again, everything that can be used for good can also be applied by fraudsters. Fraudsters use this to create, within a few clicks, multiple instances of the devices.”
If you’re an organized fraudster, emulators are an excellent way to get more bang for your buck. Instead of going out and buying multiple mobile devices, you can use a laptop or desktop computer to create multiple virtual devices that work the same exact way.
Combined with app cloners—tools that allow fraudsters to run multiple instances of an app on the same device at the same time—a bad actor can supercharge their multi-accounting and fraud operations.
The image below is a screenshot from Eduardo’s presentation during the About Fraud webinar linked above.
Eduardo explains the image, “Here's an example of the emulators being combined with app cloners. We initially had one single device with multiple instances of Telegram. Now, we have devices, each of them with ten Telegram clones. That's a very, very powerful and dangerous tool, because the fraudsters can commit attacks pretty much exponentially.”
Image injection tools
Gig economy apps know that consumer trust is one of their most crucial resources. If consumers don’t trust your platform enough to order food, hail a ride, ride a vacation stay, and so on, you won’t have user retention, and your platform won’t thrive.
Many gig apps have adopted more stringent identity verification measures as a Trust & Safety advancement, including ID + selfie verification at onboarding or at the start of worker shifts.
Naturally, this is a stopgap for fraudsters (as it’s intended to be), but it’s by no means a complete blocker. Selfie verification is meant to be taken directly from the device’s camera to ensure that it’s a live photo of the actual account holder—otherwise, fraudsters could upload photos or videos from the device’s camera roll instead, hiding their true identity and staying on the platform.
Image injection tools enable fraudsters to bypass the onboard device camera and do just that. In the images below, we can see an image injection tool that allows us to upload a photo of a cute puppy from our camera roll, instead of using the device’s camera as intended.
Location spoofing app
Location spoofing apps are a FaaS tool that helps fraudsters defraud location-based gig apps, like ride-hailing and food delivery. Using a GPS spoofer app, for instance, a fraudster can falsely claim to have delivered orders that were never picked up or were kept by the fraudsters; they can also use location spoofing to falsely claim to have started a shift in areas where hourly pay is mandated.
Stopping Fraud-as-a-Service tools with tamper detection
The good news is that fraud-as-a-service tools like the ones referenced above leave traces of their presence on a device. At onboarding, tamper detection technology can be used to check the integrity of the device and look for signs of emulation, tampering, GPS spoofers, image injectors, and more.
In the case of Incognia’s solution, the presence of any of these things raises a device’s risk assessment rating, allowing platforms to make a more informed decision about the types of devices and tamper risk they allow to join and work on their platform.
To learn more about Incognia’s tamper detection capabilities, visit our solutions page here.