54.5%
Device Identity Frontline Report
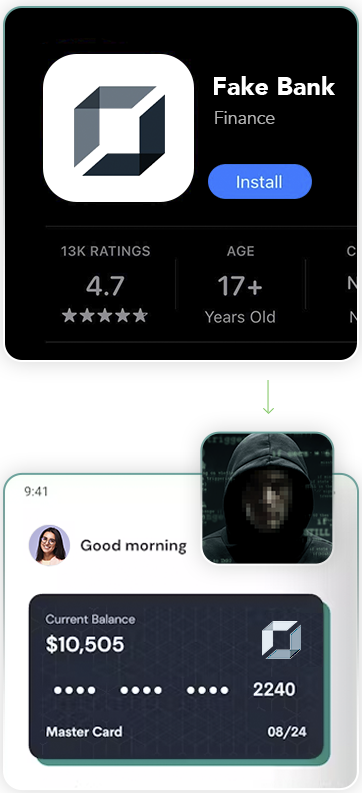
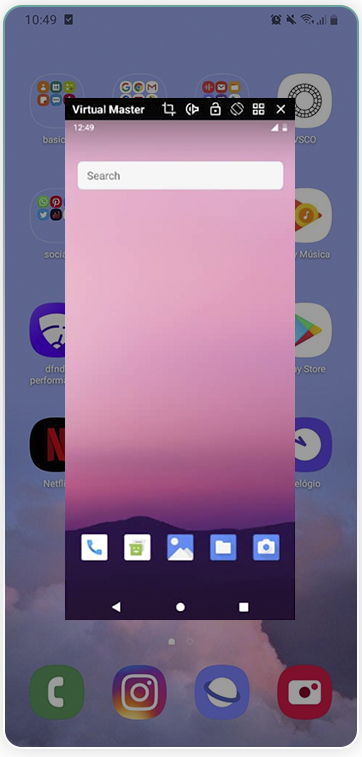
Fraudsters are constantly developing new ways to up their game and escape detection — but fortunately, so are fraud prevention experts.
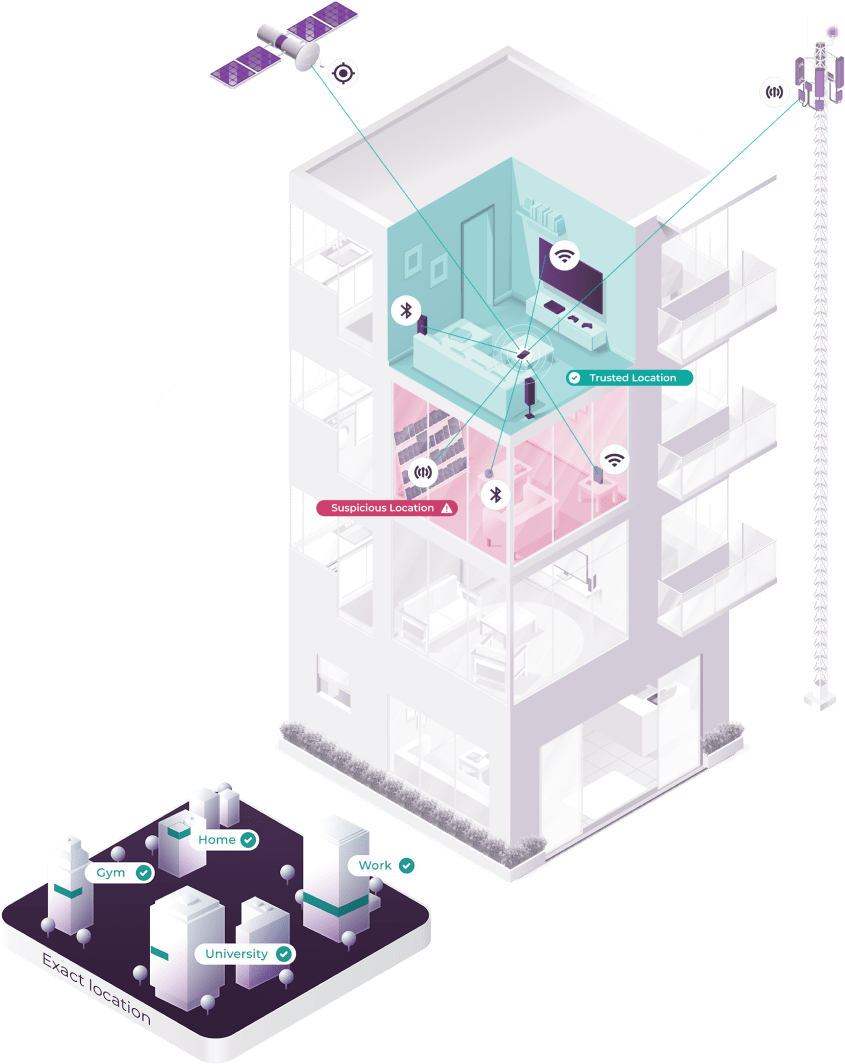
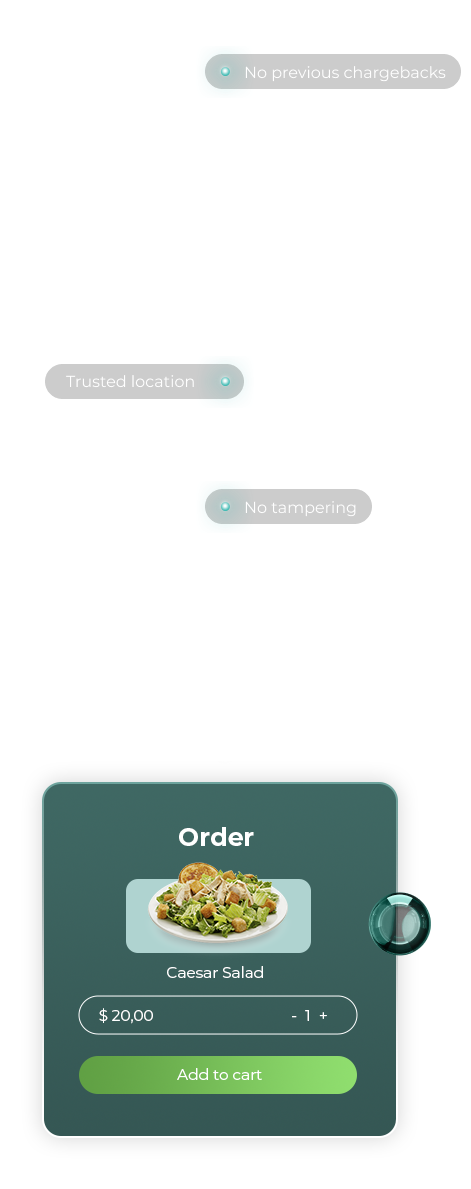
Some of the most resilient and accurate signals at our disposal today?Device and location.
In this report you’ll learn the insights we uncovered from our network in 2023, including
Behaviors that identify legitimate and risky users and devices
Trending and new types of threats to watch in 2024
Strategies and tactics to stay ahead of the evolving fraud landscape





.png)



.png)





.png)




.png)
.png)