What is Authentication? [The essentials of digital authentication]
Authentication is a security process to verify if a person or object is genuine and true to what is claimed. The act of authenticating a person, an entity, or an object is not new, since the root word for "Authentic" is from the Greek "authentikos", which means "original, genuine". So the act of authentication is comparing and matching to determine if something or someone is what or who they are claiming to be.
A brief history of digital authentication
Authentication for computers began around the 1960s when passwords were first stored in a database and the user's password entry had to match what was in store. Even though authentication has evolved, since the 1960s and 1970s as cryptography has come into play, passwords are still the norm and most used method of authentication.
Around 40 years ago, when it was recognized that passwords were not infallible for digital authentication, Dynamic Passwords were born. Then, when computers began to have higher processing power, it was possible to develop and employ one-time passwords (OTP) as single-factor or even as multi-factor authentication.
By the end of the 1990s and the beginning of the 2000s with the widespread use of the internet, an unprecedented volume of sensitive data was being handled by websites, such as e-commerce and financial institutions. The need for stronger authentication led to the increasing use of Multi-factor authentication (MFA) including the use of the password along with another form of authentication such as an OTP, knowledge-based questions, or the use of an authenticator app. The combination of two or more factors increased the strength of the authentication.
The launch and widespread use of mobile phones has brought to the public additional types of technologies, previously restricted to experts and government agencies, such as the use of biometric authentication including fingerprints, retinal, voice, and facial recognition. Behavioral biometrics and recognition signals recently are also taking an important role in authentication.
Even though authentication methods have evolved through time, it is extraordinary that even today the most widely used methods, at least in mobile banks, are still passwords and OTPs, two of the least secure types of authentication.
It is critical in authentication that a layered approach is adopted, and that is the biggest contribution all the new methods can provide since there is no silver bullet.
The biggest and most important evolution about authentication is the increasing deployment and adoption of frictionless and user-friendly methods that do not require the user to be a security expert.
Authentication vs. authorization
Both user authentication and authorization are important for security. Authentication confirms the identity of a user, and authorization grants access to a user, so it is fair to say authentication is a prerequisite for authorization.
How does authentication work?
The objective of authenticating a person in today's digital systems is to prevent unauthorized personnel from accessing certain accounts, physical or digital environments. Authentication ensures that only legitimate users are granted access by recognizing and matching credentials that were previously registered to an individual. If the credentials provided match the user can be authenticated. If the credentials provided do not match, there is a risk there is a bad actor trying to get unauthorized access.
The most common authentication method is single-factor authentication, but depending on the risk of unauthorized access, it is recommended that multi-factor authentication is adopted.
Single-factor authentication requires users to authenticate with only one type of evidence for authentication, which, most of the time, is a password. Multi-factor authentication is accomplished with a layered approach, with two or more types of authentication.
What Is Multi-Factor Authentication?
MFA is used to authenticate if the identity of a user is genuine. It requires a user to present two or more pieces of evidence, or factors, for authentication. A key goal for MFA is to add additional authentication factors to increase security. The well-designed multi-factor authentication strategy strives to maintain a balance between added security and user convenience.
Types of Multi-Factor Authentication
MFA requires the use of multiple (at least two) factors to verify authorized access by the user. There are three main types of authentication factors used, and for each factor, there are different methods for authentication:
Knowledge - Something you know
It typically includes information that is known only to the user. The combination of a username and password or PIN is the most common example of a knowledge factor. Some organizations may require security questions such as the mother’s maiden name or the name of the school first attended to verify the user’s identity.
Possession - Something you have
The possession authentication factor is helpful when users have something specific in their custody, such as physical tokens, smart cards, key fobs, or mobile phones. Google authenticator is a good example of an app on the phone as a token. It is unlikely that a hacker who has stolen a user's password also has stolen their physical possession as well. This type of authentication may include confirming through a pop-up notification on a mobile phone or requiring the insertion of a security card, or even, the outdated and deprecated one-time password, which could be provided via text message or email.
Inherence - Something you are
The inherence factor uses behavior or biological traits of the users for login purposes. Commonly used inherence factors include fingerprints, retinal scans, or voice or facial recognition. Behavioral biometrics and recognition signals are also inherence factors since it is difficult for fraudsters to mimic or fake user behavior. This type of authentication is considered to be not only strong but also the type with the lowest friction for users.
A comparison list of MFA methods, with a ranking of both levels of security and friction, is shown in the following table
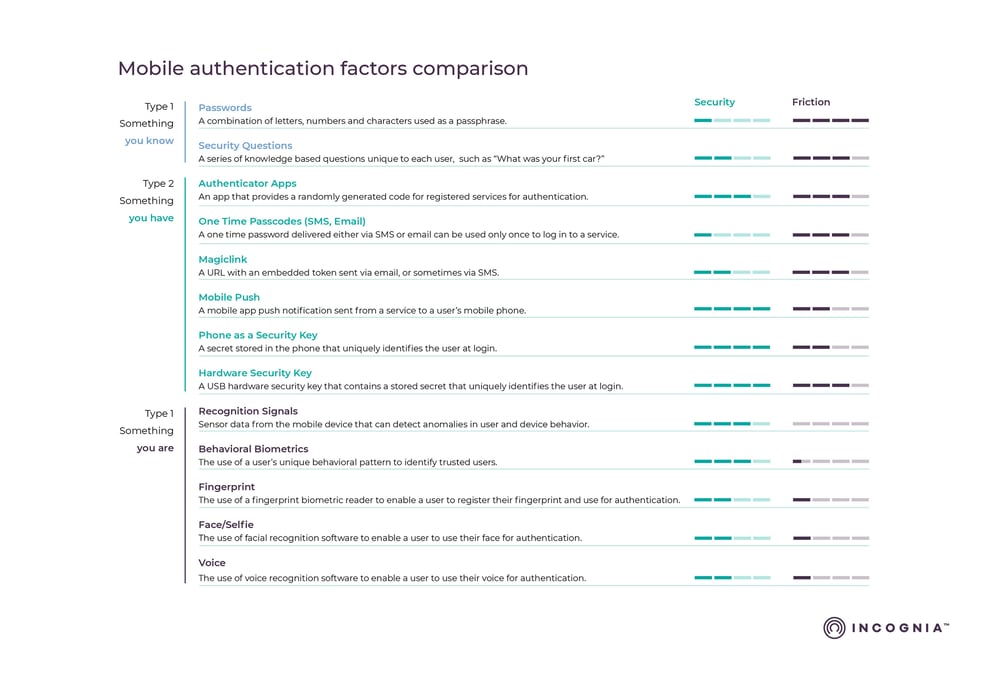
Applications may use combinations of these factors and authentication mechanisms that best suit the application, costs, IT structure, and security strength that is required. An example of multi-factor authentication is login to a mobile bank, which after requiring a password (knowledge) for login for users to gain access to the account, additionally prompts the user to input a number from an authenticator app on the mobile phone (possession). Another valid example is login to a fintech app using zero-factor authentication enabled by location behavior (inherence), which would enable a passwordless login and money transfer for the user. If the user location behavior does not match the user location behavior history pattern, the use of an authenticator app could be required as an additional factor to generate the necessary token for validation, thus authenticating the trusted user, or preventing the access of a fraudster.
What is two-factor authentication?
2fa or two-factor authentication, also referred to as 2-step verification, is a security method requiring users to present two factors for authentication for accessing an account. There are still questions about the differences between 2fa and mfa, but the bottom line is, 2FA is a subset of MFA, so all 2FA is a MFA, but not all MFA is a 2FA.
What are the biggest challenges for mobile authentication?
As companies look to launch and grow mobile services the two biggest challenges are balancing the need for increased security, while ensuring a great user experience.
Minimizing friction for a superior user experience
The average human’s attention span has been shrinking, from 12 seconds in 2000 to 8 seconds in 2015, and on mobile, users have particularly short attention spans. Part of the attraction of mobile for consumers is the ability to get instant information and make instant decisions and selections. When security adds friction and slows down access to information and mobile services, the result is increased abandonment rates and lower conversion rates. This need for an instant response from mobile services is why minimizing friction is the #1 concern for delivering a superior user experience on mobile.
Ensuring the security of user accounts
With the increasing adoption of mobile, it is no surprise that fraudsters are now shifting their focus to mobile. Fraudsters are exploiting weaknesses in authentication methods including in passwords, OTP over SMS, and biometrics with the goal of account takeover. And this is where the tug of war between security and friction comes into play. The risk of fraudsters and cybercriminals accessing user accounts on mobile has led to increasing focus on security controls, which unfortunately are also keeping legitimate customers out.
Best Authentication choices for mobile
In reviewing the authentication options it is evident that authentication factors rank differently for security and friction. No authentication solution offers both the strongest security and least friction. The good news is that given multi-factor authentication requires two or more authentication factors it is possible to combine authentication factors to get the optimum balance of security and friction.
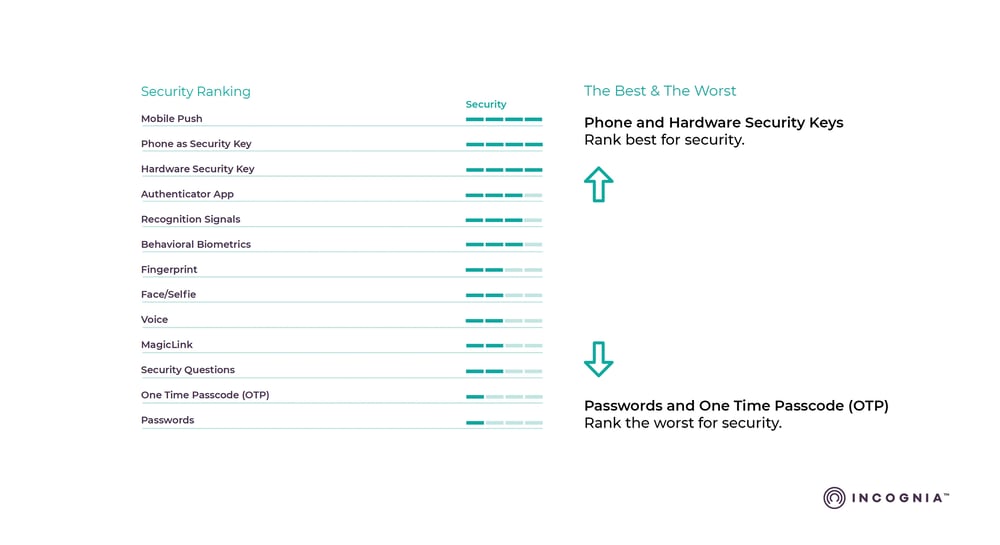
Given that passwords and one-time passcodes (OTP) rank the lowest for security it is hard to believe that passwords are still the prevalent method of security, and that one-time passcodes (OTP) are the most commonly used second factor for authentication.
Passwords offer the weakest security
The issues with passwords are now widely understood. With users today managing on average 70 - 80 accounts, they inevitably use simple passwords such as 1234 or reuse passwords across sites, when they can. Forgetting passwords is the number one customer support issue, creating friction for the user and operational costs for companies. Large-scale data breaches and increasing use of social engineering scams are leaving users vulnerable to account takeover from the use of stolen credentials.
OTP over SMS - Security Weakness
The use of OTP over SMS has been under scrutiny by security professionals for the past few years. In the NIST Identity Guidelines, it is designated as a restricted form of authentication because it can be easily misused by fraudsters. SIM swap fraud came onto the scene back in 2017 and became a go-to method to take over accounts.
Biometrics - Security and Bias Concerns
While users have shown interest in using fingerprint sensors, facial and voice id, there are increasing concerns about the theft of biometric data and also how these types of recognition technologies can introduce bias into our use and accessibility to technology. Biometric data, like passwords, when centrally stored on servers are also vulnerable to theft and forgery, and unlike passwords that can be changed or updated, we cannot change our fingerprints or facial, voice ids. Biometrics stored locally on a device is more secure but requires users to go through the added friction of registering their biometrics separately on each device. Also, the use of facial, or selfies, now incorporates liveness detection to combat the use of photos as a substitute for the real person, however, deek fake technology is now showing the ability to fake the liveness detection.
Bias is also a concern with the use of biometrics for fraud prevention and other applications. The performance of facial and voice recognition software is dependent on training data, and the concern is that data sets that are biased towards types of faces or voices have the potential to introduce bias into the results. For fraud prevention, this could mean that certain ethnicities would be flagged as high risk at a greater rate because they were not well represented in the training set.
Recognition Signals & Behavioral Biometrics - Dynamic Security
Recognition signals and behavioral biometric-based authentication methods leverage unique human behavior, however, there is a key difference between biometric and behavioral biometrics. This is that behavior patterns, while unique to each person, are also constantly changing and updating, and therefore compared with a static identifier, such as a fingerprint or face ID, behavioral biometrics create a dynamic authentication factor that is very difficult to mimic or fake.
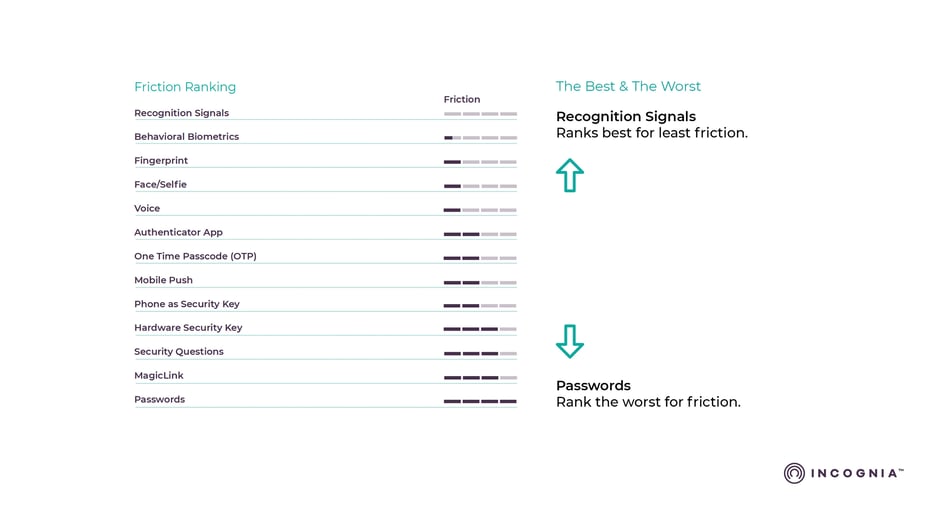
Recognition Signals & Behavioral Biometrics - The lowest friction
The reality is that today’s mobile devices are loaded with sensors that provide valuable information on user behavior. Recognition signals and behavioral biometrics take advantage of this data to identify unique patterns for each user. One key difference between recognition signals and behavioral biometrics is the time for the models to learn and provide risk assessments. Recognition signals offer immediate risk signals, from time zero, while behavioral biometric models can take an extended time to learn, days or weeks.
There are many types of signals and behavioral biometrics that have been used for fraud detection. Mouse movement and typing speed have been used extensively for desktop, and laptop applications, however for mobile the strongest signal is location behavior.
Location as the Strongest Trust Signal on Mobile
Of all the recognition signals, location is the most relevant for fraud prevention on mobile.
In today’s world, mobile devices have become an extension of ourselves. We carry our phones with us everywhere, and every person’s movements in the world are unique and create unique location behavior patterns. Mobile devices today contain many sensors that relate to motion and position and also the status of the device.
Combining MFA with risk-based authentication offers the opportunity to provide an initial low friction authentication option to users and only invoke higher security, higher friction, authentication methods for the high-risk logins or sensitive transactions.
Key Takeaways
- There are many authentication choices
- Authentication factors rank differently for security and friction
- The use of recognition signals or behavioral biometrics offers the least friction authentication method and can be used for zero factor authentication
- Hardware security keys offer the most secure authentication method
- Risk-based authentication with MFA delivers the best balance of security and friction